Hackers are getting more sophisticated. As a result, the minimum security protections that businesses need to defend against cyber criminals have changed.
Cyber criminals have advanced the technology they use to sneak in (or bust through) network doors, so the list of must-have cyber security basics has expanded.
To have a fighting chance, you need a layered cyber security strategy.
It might be hard to know what those layers should be if you’re not a technology specialist. You might even have a gut feeling that what you’re doing right now isn’t enough. So we’re here to help.
Here are 17 foundational cyber security measures that small and midsize businesses need in 2022 to protect against today’s (and future) threats.
Cyber Security Basics For a Strong Foundation
- Anti‐Virus / Anti‐Malware
- Anti‐Spam
- Patch Management
- Firewall Management
- Wi-Fi Permissions
- Windows Log Alerts
- Password Policy
- Multi‐Factor Authentication
- Secure Internet Gateway
- Gateway Anti‐Virus
- Office 365 Email Encryption
- Backup and Disaster Recovery
- Active Directory Management
- Endpoint Detection & Response
- Annual Internal and External Vulnerability Scans
- Security Awareness Training
- Cyber Liability Insurance
1. Anti-Virus / Anti-Malware
Hackers have many methods of installing malware on computers. Whether it’s through a compromised website or clicking a link in a phishing email, viruses, worms and trojans can wreak havoc once they’ve made their way onto an employee’s computer -- and then to your network.
Once in place, malware can monitor and steal information from your system, encrypt your data and demand a ransom, or cause other damage, including corrupting your hard drive.
Anti-virus and anti-malware have long been cyber security standards, and they continue to be a must-have layer of defense. These programs scan the devices on your network, looking for known malware. Once found, the unwanted program is quarantined so that it can’t spread. Then actions are taken to remove it from the affected devices.
2. Anti-Spam
Anti-spam programs prevent fraudulent email messages from entering your inbox. Spam emails can appear to be from people or organizations that you know, like an executive at your company or a business that is well known like UPS or Amazon.
Through social engineering, these messages entice people to click on a link or open an attachment which then downloads a malware payload.
Anti-spam software works using a system of protocols to identify unwanted messages and stop them from entering the user’s inbox.
With the most modern anti-spam software, you can customize settings according to your needs. This allows you to approve some emails, which might seem like spam, to enter your inbox. You also have the option of creating a personal whitelist, allowing specific senders while blocking others.
3. Patch Management
Patch management refers to the maintenance you do to software to close vulnerability holes. Software developers support their products by regularly releasing updates as weaknesses are detected. In addition to patching newly found security holes, updates can also include changes that improve the performance of the software.
Cyber criminals actively look for computers that are running unpatched or out-of-support software so that they can exploit known vulnerabilities. This includes your operating systems and any software that you’re using on your servers, workstations, laptops, and connected devices.
Your IT team should be reviewing, testing, and deploying patches on an ongoing basis.
4. Firewall Management
Firewalls are the primary barrier between your sensitive data and cyber criminals.
A firewall examines all incoming and outgoing traffic on your network. It controls this traffic by following sets of rules that determine what is allowed and not allowed – or trusted and not trusted.
Firewalls need active management to ensure that there aren’t any holes where cyber criminals can sneak in. This includes proper configuration, testing, and regular updates. Employees working from home should also have firewalls on their home network.
5. Wi-Fi Permissions
Granting Wireless Internet access on a limited basis is an easy way to cut down on the possibility of an attack. Wi-Fi permissions should also be set to ensure only authorized users can do specific activities on your network.
If you regularly have guests such as vendors, contractors, and friends visiting your office, you should set up a separate guest Wi-Fi network. Doing this allows them the benefit of internet connectivity at your facility while keeping confidential information out of their hands.
6. Windows Log Alerts
Your Windows operating system has the ability to keep a record of all the activity that takes place on your computer. Network administrators use some of the information gathered to monitor and tweak performance, while some data is related to security.
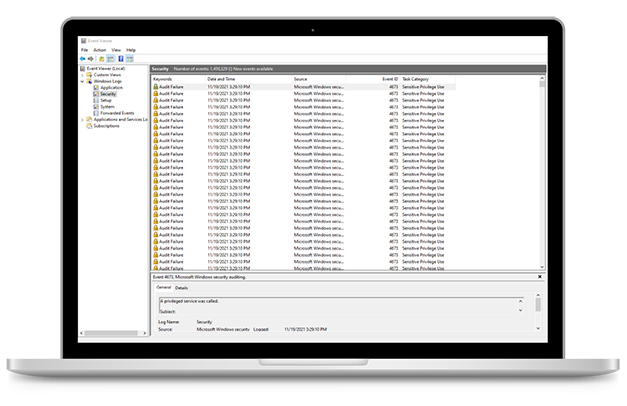 As security logs are created, they can send out automated alerts when there’s something suspicious. For example, a login attempt from a specific geographical location could mean a hacker is trying to force a password. Another example is an excessive use of computing power, signaling that the computer has possibly been commandeered into a botnet.
As security logs are created, they can send out automated alerts when there’s something suspicious. For example, a login attempt from a specific geographical location could mean a hacker is trying to force a password. Another example is an excessive use of computing power, signaling that the computer has possibly been commandeered into a botnet.
7. Password Policy
According to Verizon’s 2020 Data Breach Investigations Report, about 80 percent of breaches due to hacking involve stolen, lost, or weak passwords. This is mainly because most businesses do not enforce password policies.
A password policy is a specific set of rules meant to enhance the security of your network. It mainly involves encouraging users to set up strong passwords and use them properly.
We advise that you change your passwords every 2-3 months.
Most organizations include password policies in their company handbook or separate Acceptable Use Policy.
Some organizations set up programs to train their employees on security and effective password-setting techniques. For instance, a password should not be obvious or based on personal information that can be easily found, such as birthdays or anniversaries. In addition, strong passwords should consist of a combination of upper and lower-case letters, symbols, and numbers.
8. Multi-factor Authentication (MFA)
Multi-factor identification (MFA) is becoming increasingly popular as a means of securing the login process.
MFA works by requiring an individual to take an additional step to verify their identity when logging into an account. It works because it’s highly unlikely that a hacker would have both the correct password and the means to complete the next step, like inserting an MFA code that is received on their mobile device.

You can combine MFA with windows log alerts that notify you when someone logs into one of your accounts or an account you monitor. The alerts send you an email or text message any time an event of interest occurs, so you can verify that the login is legitimate or not.
9. Secure Internet Gateway
If you’re doing any operations over the internet (and who isn’t?), you need the additional protection of a Secure Internet Gateway for the traffic going in and out of your network to the web.
It’s similar to (but not the same as) a firewall. It’s basically a protocol that helps establish secure connections to your network, websites, and other systems online. It works by blocking any unsecured traffic from coming into your internal network.
Businesses use Secure Internet Gateway as another layer of security to protect their users from any malicious internet traffic or suspicious malware as they browse. It’s especially useful for remote workers or devices being used in other locations outside the office.
10. Gateway Anti-Virus
Modern firewalls have additional capabilities that help businesses build up the digital perimeter around their network -- gateway anti-virus is one of them. This program works like standard anti-virus in that it looks for known malware programs and takes action to shut them down.
Your firewall’s job is to control traffic in and out of your network, so having gateway anti-virus allows you to spot and shut down malware in emails or web pages BEFORE they even get to employee workstations and laptops.
Humans are prone to make mistakes and can be manipulated into clicking, downloading, or browsing that triggers a malware download. Gateway anti-virus means you’re putting one more layer between the bad guys and your employees.
11. Office 365 Email Encryption
Microsoft Office 365 is one of the most convenient office applications that businesses use nowadays. The cloud-based platform gives people the tools they need and enables collaboration through various email and calendaring applications and Microsoft Teams. Plus, you can use it on any device, at any time.
However, the fact that it is online-based makes it prone to hacks, and this is where Office 365 Email Encryption comes in. It has various encryption options you can use to enhance security for emails sent in Office 365. You can also encode any sensitive information you might want to send and have it so that only the intended party can decode it.
To create a secure message, just create a new email in Outlook and select the ‘Options tab,’ then choose the Encrypt option and click on the restrictions you want to set up.
12. Backup and Disaster Recovery
In the event that hackers manage to penetrate your security perimeter and processes, you need to have a contingency plan. Data backup and disaster recovery are essential components of your response. Your backup plan should be based on what data you need to resume operations and how long you can afford to be down. These are known as your recovery points.
Data backup used to be considered insurance against ransomware because all you needed to do would be to restore your system if your data was taken hostage. Not anymore. Cyber criminals are now using extortion to get organizations to pay their ransom, threatening to expose data for all to see on the web.
Back up your data as part of your incident response plan, but don’t rely on it to be your ONLY response.
13. Active Directory Management
Active Directory acts as a central user management tool and is essential for security in a couple of ways.
First, it’s a way that you can enforce some of your data access policies. Through Active Directory, you can allow or deny users access to specific folders and files based on what they need to know for their job role.
If behavior of a user falls outside of the permissions that are in place, then Windows Log Alerts can trigger a notification. Follow-up is then needed to determine if the behavior was a genuine threat or just an error.
Active Directory has security features that are very familiar to hackers, so proper management is essential -- imagine what a bad guy could do if they stole the ability to change accounts and permissions! Proper management includes configuring the program so that it’s not set at default for security, and diligent password and identity management by the administrators who have control.
14. Endpoint Detection and Response (EDR)
While anti-virus scans for known malware, you need to protect your network from unknown malware.
This is where Endpoint Detection and Response (EDR) comes in. EDR is software powered by Artificial Intelligence (AI) that studies your network and determines what is normal behavior. Then, when something abnormal happens, it stops it and sends an alert.
 EDR was developed in response to cyber criminals’ evolving tactics. If you’re only defending against known malware, you’ll always be behind.
EDR was developed in response to cyber criminals’ evolving tactics. If you’re only defending against known malware, you’ll always be behind.
EDR should be deployed on all of the devices that are connected to your network, from workstations and laptops to tablets and Internet of Things (IoT) devices.
15. Annual Internal and External Vulnerability Scans
Vulnerability scanning is the process of actively searching for network security issues. Unlike a full penetration test where an ethical hacker manually tries to exploit your vulnerabilities and break in, a vulnerability scan is a tool that scans the surface to show weaknesses. It gives a score depending on the type of vulnerability it finds.
This should be done annually at a minimum. While more frequent scanning is preferable, annual scanning for internal and external vulnerabilities will help you set a baseline for your security posture and show progress on your risk profile over time.
Not so fun fact about vulnerability scanning: attackers can use these same tools to find the external weaknesses on their victims’ networks. That’s why running the scans regularly and remediating the issues they discover is critical.
16. Security Awareness Training
Any IT security professional will tell you that the weakest link in a company’s security is its employees. Hackers use social engineering techniques and phishing to exploit unsuspecting employees to extract sensitive information and access computers and networks.
This can all be countered with ongoing employee security awareness training programs. This is where all employees who have access to your network are formally trained on all the best practices involving security. They are educated about the system’s common security threats and vulnerabilities and how they can be coaxed into allowing a security breach.
The goal of training is to teach each member of the team to actively spot clues that indicate threats and use this to prevent potential cyber attacks.
For best results, security awareness training needs to be a continuous process, included when onboarding new employees, and ongoing to keep all employees updated with the latest trends in the field.
As a manager, you'll be able to see high-level and granular views of your risk points, so you'll be able to take action from there.
17. Cyber Liability Insurance
You’re probably thinking, “If I’ve implemented all of the appropriate security measures to protect my data, do I need cyber liability insurance?” Fair question. Our advice is: yes.
Cybercrime is on the rise, and we’re fighting an uphill battle.
Bad actors are constantly developing new ways to break in. You don’t want one unintentional click to be the reason why you’re out hundreds of thousands of dollars or worse – out of business.
When you need it, you’ll be thankful to have cyber liability insurance available to cover remediation costs, reputation management costs, potential ransom payments, legal fees, and the many other costs you may encounter in the process.
Strategically Combine Layers for Best Cyber Security
While this article describes many cyber security tactics, the way they’re combined makes a big difference in how effective they will be. You can’t just cobble together a bunch of tools and hope for the best. Instead, when you have experts at the helm, you’ll get your best protection, determining what technology tools will create a strong defense and supporting them with non-technical policies that guide employee behavior.
Related: Executive Guide to Cyber Security: Essential Information for Managing Business Risk
Cyber Security Assessments
It can be challenging for a small IT support team to manage cyber security for businesses. Cyber security is a specialized expertise that’s different from traditional IT management.
VC3 is an MSSP and Managed IT Service provider. We offer cyber assessments and partner with companies to create a security strategy that meets evolving cyber risks. Contact us, and we’ll get you the information you need to evaluate your current security measures properly.


