It’s easy to fall behind on the latest technology lingo. After all, new information technology (IT) buzzwords and acronyms pop up on a seemingly daily basis.
We’re here to help.
We’ve compiled a list of 7 IT buzzwords you’ve probably heard but may not know exactly what they mean, why they’re important, and how they relate to your business.
- Everything-as-a-Service (XaaS)
- Multi-Factor Authentication (MFA)
- Artificial Intelligence (AI)
- Vulnerability Scanning
- Endpoint Detection and Response (EDR)
- Business Intelligence (BI)
- Cyber Liability Insurance
Keep in mind that just because they’re considered “buzzwords” doesn’t mean that they’re fads. With a more complete understanding of these technology buzzwords, you can take advantage of the increased productivity, security, and risk mitigation that comes along with them.
Let’s jump in.
1. Everything-as-a-Service (XaaS)
Everything-as-a-Service (XaaS), pronounced zass in the tech world, is related to cloud computing and the subscription-based world we live in today.
Instead of having software or hardware locally in your office onsite, it all lives online. This could include but isn’t limited to infrastructure, applications, or even your network. For example, many businesses now use Office 365 or G Suite, which are both XaaS. With these services, your email server is now hosted in the cloud and not physically in your office as it was in the past.
Any service your business uses that is hosted in the cloud is considered XaaS.
2. Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) has quickly become an essential piece of business cyber security.
MFA validates the identity of a user when logging into an account by requiring verification with an additional step, adding an extra layer of protection.
You’ve almost certainly experienced this before with your bank, email, or even Amazon. It’s common for consumer services, and it’s considered a necessity for businesses as well now too.
MFA tools work by sending a temporary code through either a mobile app or a fob that the user must put in before being granted access. This ensures that an attacker wouldn’t be able to access any data without the code, even if they somehow had the password.
MFA doesn’t replace other security layers. It's one more layer to help protect you from unwanted intrusions.

3. Artificial Intelligence (AI)
It seems like EVERYONE is talking about Artificial Intelligence (AI). What’s surprising is that the term isn’t actually new at all. AI was coined in the 1950s and has grown in popularity as technology advances more quickly.
A math professor at Dartmouth College, John McCarthy, was the first to give AI a concrete definition:
“Every aspect of learning or any other feature of intelligence can in principle be so precisely described that a machine can be made to simulate it.” CBS.com
In other words, AI is when hardware or software is so intelligent that it actually learns. So it’s not just programmed to do something, but it’s learning. This is also known as Machine Learning or Deep Learning.
An engineer creates protocol for the machine to look for, and as it’s finding it, it learns something. It’s kind of like repeating the ABCs to a child -- over time, they learn the song and how each letter makes up words.
Many cyber security tools today rely on AI to help detect and prevent cyber security attacks.
4. Vulnerability Scanning
Vulnerability scanning is a process that proactively looks for known weaknesses in your network.
There are two common types of vulnerability scans: external and internal.
Think of external vulnerability scanning as “scanning the perimeter.” The scan attempts to connect to all of the systems on your network, then compares the data it gets back to a large library of known exploits and weaknesses, letting you know where your weak spots are.
Internal vulnerability scanning is when you provide system credentials to the tool and let it inside your network. Once it’s in, it can look more thoroughly for things like missing patches, weak configurations, and out-of-date code libraries.
These scans help your IT support team get better insight into your network’s security so they can more effectively update, patch, and otherwise mitigate known vulnerabilities.
Keep in mind, external vulnerability scanning can be used by hackers looking to compromise your network. Running vulnerability scans proactively on a regular basis will help you find and fix vulnerabilities before an attacker does.
Related Resource: 17 Foundational Cyber Security Measures Businesses Need
5. Endpoint Detection and Response (EDR)
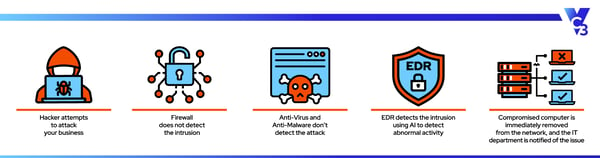
Endpoint detection and response (EDR) picks up where your firewall and antivirus leave off. Those tools (and many others) block known threats – EDR battles the unknown.
EDR is a cyber security layer that monitors and analyzes the activity on your network to establish a baseline for what’s normal. Once it knows what’s considered normal, it can easily identify what’s abnormal. That’s where the magic happens.
Once it detects abnormal behavior, it can automatically block the activity and/or remove the potentially compromised device from the network to prevent further infection when a threat is detected. This notifies your IT support team so they can remediate the issue.
With the increase in zero-day exploits (and cyber attacks in general), it’s critical to have tools like EDR to protect your network.
6. Business Intelligence (BI)
Business Intelligence (BI) is a set of tools used to capture, store, and analyze a business’s data.
BI tools take the data already being generated by your company and compiles it all into one place. It turns that data into knowledge that can be used to help make informed business decisions.
Up until recently, BI tools were primarily used by large businesses due to their cost. But with the business world rapidly moving away from on-premises services to cloud-based services, BI has become a lot more cost-effective for small to medium-sized businesses, giving them a competitive edge.
7. Cyber Liability Insurance
If this is the first time you’ve heard the term cyber liability insurance, it won’t be the last.
With the increase in cyber attacks, businesses are trying to find any way to mitigate the financial impact when an attack eventually does occur. The financial repercussions of a cyber incident can be crippling.
That’s where cyber liability insurance comes in.
Cyber liability insurance is a policy that helps a business financially recover from a cyber attack. Depending on your policy, it helps cover some or all of the costs to help pay ransomware demands, legal fees, regulatory fines, and the fallout from reputation issues.
Cyber liability insurance is not a replacement for cyber security. In fact, to get the best rates and coverage, you’ll need to have several security basics in place.
Having cyber liability insurance as part of your comprehensive cyber security plan is a great way to ensure that your business and data are safe, and if you are the victim of an attack, you can financially recover.
Apply Your IT Buzzword Knowledge to Your Business
And there you have it, 7 information technology buzzwords that you can’t afford to ignore. Knowing each of these IT buzzwords and their importance will help you improve your security posture, make business decisions, and achieve your business goals.
Not sure if your Southern California-based business is set up for technology success? Reach out to us anytime. We’d be glad to help evaluate your IT situation.


