Imagine this – one of your employees clicks on an email phishing scam that leads them to a very real looking login page for Microsoft 365. They enter their login information, giving a cybercriminal the credentials they need to access your company’s email. The employee thinks the extra login was a fluke and continues with their day.
Meanwhile, the cybercriminal logs into your email system and lies in wait.
They watch the emails flow in and out of that user’s mailbox. They learn who your customers are and start communicating with them as you. They kindly let one of your biggest customers know that your banking information has changed. Before you know it, your customer sends $150,000 to a bank overseas instead of to you.
Not only is this a major loss for your customer, but it’s also damaging to your reputation.
This type of situation happens all the time.
It can happen with an email system, application, or any other compromised system or device. In a lot of cases, cyber criminals don’t even need you to explicitly type in your credentials in order to steal them. They trick you into downloading malware, then get the info they need once they’re in your network.
Hackers are creative and go to great lengths to socially engineer people into doing things for their benefit. Humans are the weakest link in cyber security, so having several layers of security to protect your systems is important.
Luckily, there’s a simple step that can stop hack attempts like these in their tracks – multi-factor authentication (MFA).
We can all agree that we’d rather the hacker didn’t get in in the first place, which is why MFA doesn’t replace your other security measures. It’s an extra layer of cyber security protection that’s on the must-have list for businesses today.
This article will help you understand what multi-factor authentication is, what your options are (there are a lot of choices these days), what’s different between them, and how much they cost.
What is Multi-Factor Authentication?
In short, multi-factor authentication (MFA) is the process of verifying your identity more than once to access to a system.
For example, to withdraw money from an ATM, you need the bank card and the PIN number – without both pieces, you won’t be able to complete the transaction. This prevents unauthorized people from getting access to your account.
The same concept exists with multi-factor authentication (MFA) for business technology. It helps combat weak passwords, data breaches, social engineering, and phishing attacks because it requires that extra identity confirmation before letting someone.
According to Verizon Business’s 2020 Data Breach Investigations Report, credential theft and social attacks, such as phishing and business email compromises, are responsible for the majority of breaches. That’s why this extra step is critical.
If you think back to the example scenario I mentioned previously, multi-factor authentication would have stopped the hacker from being able to log into that user’s mailbox. They had the credentials, but they wouldn’t have been able to get the extra code or push notification to log in successfully.
What Are Multi-Factor Authentication Options for Businesses?
There are many different options for multi-factor authentication (MFA). Trying to figure out the right one to fit your organization’s needs can be overwhelming.
Here’s a breakdown of the general types of MFA solutions and why some are more effective than others.
Comprehensive Multi-Factor Authentication Solutions for Businesses
Businesses have complex needs when you consider the number of technologies that may require MFA – domain login, email, applications, terminal server, etc. Finding the right solution that integrates with all (or at least most) of the technologies your business uses is ideal.
Two great choices for comprehensive MFA are WatchGuard’s AuthPoint and Cisco’s Duo.
These multi-factor authentication solutions give 360-degree coverage to your domain, applications, email, etc. They’re both cloud-based and offer second-source validation.
They use industry-standard authentication technology, which allows them to integrate with a vast library of other systems. Having a tool that’s as agnostic and broad as possible allows you to connect nearly all your organization’s applications and devices in one place.
This gives you the 360-degree coverage you need to plug your potential entry points.
You and your users have one hub for MFA, so they don’t have to switch between different authentication apps for different services, or rely on SMS text codes (which have highly publicized vulnerabilities.)
Though there are many other choices for comprehensive MFA, WatchGuard's AuthPoint is our preferred solution. We evaluated many other vendors and ultimately chose AuthPoint because the technology is solid, it integrates with a wide range of systems, it uses industry standards, it’s simple to deploy and manage, the price point is right, and WatchGuard has great support.
How Do Comprehensive Multi-Factor Authentication Tools Work?
These types of MFA tools are user-friendly, which is important when you’re rolling it out to a workforce with varying levels of tech-savviness.
To use these systems, ideally, your employees would have the app installed on their work phone. When they go to log in to their systems, a push notification is sent to their device asking if they’re trying to log in. Once they approve the login, the system will let them in.
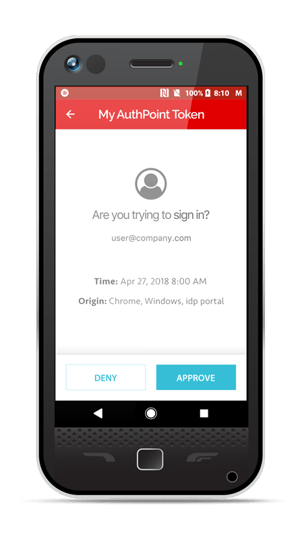 Source: WatchGuard
Source: WatchGuard
Users could also scan a QR code on the screen and enable the notification that way.
If the employee doesn’t have a company-owned device, the app could be installed on an employee’s personal phone, though some employees feel uncomfortable with that.
In those cases, employees can use a fob (pictured below) that generates a one-time code for them to log in. The challenge here is that those have a cost associated with them and, as you may expect, there’s a risk of them getting lost.
 Source: WatchGuard
Source: WatchGuard
How Much Does a Comprehensive Multi-Factor Authentication Solution Cost?
Pricing for multi-factor authentication varies depending on which technology provider you choose. For comprehensive MFA solutions like AuthPoint and Duo, you can expect to pay between $2-10 per month per user. The range scales depending on how many users you have.
What About Microsoft 365’s Multi-Factor Authentication?
Microsoft 365 has a nifty setting in it for multi-factor authentication, making it simple to implement MFA for your Office products. While that’s good news for the security of your Office products, it doesn’t protect your many other potential entry points.
It also wasn’t built to support interactive log-ins (the process of logging into your computer), which is a main vector of attack. This is a huge gap in the technology.
Enabling MFA solely on Microsoft 365 often creates a false sense of security.
Something is better than nothing, but your network will still be vulnerable since many other critical systems will be left without MFA protection – like your CRM, accounting software, ERP, etc.
Comprehensive MFA solutions like AuthPoint and Duo let you integrate Microsoft 365 -- so the other entry points are secured, and you have a central app to manage everything.
What About Microsoft Authenticator, Google Authenticator, etc.?
You may have seen that some applications give the option for MFA with Microsoft Authenticator or Google Authenticator. These tools are typically used as a one-off, though they do have paid plans available for business use.
Like multi-factor authentication for Microsoft 365, they’re better than nothing, but they still leave some areas unprotected since they don’t integrate with many business systems.
For example, your email system might offer Microsoft Authenticator as an option. Your browser-based CRM might offer Google Authenticator. It’s rare that both options are offered.
This creates two challenges:
- Your users end up with multiple authentication apps to sort through on their device each time they go to log in -- creating confusion, frustration, and delays getting in.
- It can create a shadow IT issue. Shadow IT refers to employees creating solutions that aren’t set up or monitored by your IT support team. It’s rarely done maliciously, but it creates a business problem nonetheless. What IT can’t see, they can’t manage. What they can’t manage, they can’t properly secure.
How to Choose the Right Multi-Factor Authentication Solution for Your Business
Choosing the right multi-factor authentication solution doesn't have to be complicated.
The first step to finding the right MFA solution is to evaluate your entry points and what you need to protect. Your IT support team will be able to identify the major systems, then you can work with each department to see if they use any additional applications that aren’t on your list.
Compare that list of applications and entry points with the published capabilities for the MFA providers you’re considering. Most small and middle market organizations find that AuthPoint or Duo are the best fit for their situation.
If you need any help or guidance figuring out which MFA provider would be best for your needs, feel free to reach out to us at VC3 Computer Solutions at any time. We’re happy to help.
Multi-Factor Authentication is a Piece of the Cybersecurity Puzzle
As I mentioned before, MFA doesn't replace other security layers. Foundational security pieces – like up-to-date firewalls, patches, and endpoint detection and response (EDR), to name a few – are still critical to thwarting hack attempts.
If you’re concerned about your business’s level of cybersecurity risk, or if you aren’t sure you’re protected from today’s most common scams, schedule a Cybersecurity & Risk Assessment. You’ll get a clear picture of the security holes that may be putting your organization at a higher risk level than you’re comfortable with.


