What would you do if you got an email saying your Netflix account was canceled?
“Nooooo!” might be the normal reaction, especially now when we’re all spending more time at home.
Now imagine that the email tells you that you have to re-submit your billing information.
You click. You type. You submit with your info and…you just gave a hacker your credit card number.
That’s just one scam that’s making the rounds. As if businesses didn’t already have enough to deal with, online security threats continue to grow and are more prevalent than ever.
The FBI reports an astounding 300% increase in the number of reported cybercrimes since COVID-19 hit the US in March. Here at VC3, we’ve seen an increase in cyber attacks first-hand, especially in phishing.
Cyber criminals have stepped up their game, taking advantage of organizations whose focus has been on simply remaining afloat. They’ve been particularly interested in companies with remote workers, since they know the sudden shift to remote work may have opened security gaps in a company's day-to-day operations.
Cyber predators are also very aware that people are more likely to respond to social engineering schemes like the one we described because they’re under the stress of living through a global pandemic.
The Baseline Has Moved - Advanced Security Tactics Are Now Foundational Requirements
The need for small and midsize companies to defend their IT systems from predators isn’t news – cyber security has been a challenge for them for several years. Even prior to 2020, it took 6 months on average for a small business to become aware of a data breach within one of their systems.
What used to be sufficient for security isn’t cutting it anymore. The baseline for what was considered "good security" in the past has shifted since technology has advanced and hackers have gotten more crafty.
Implementing these five security tactics will help minimize your exposure to cyber risks, protecting your company (and your people) from falling victim to a cyber attack.
1. Multi-Factor Authentication (MFA)
Inconvenient as it may be, the extra step needed to use multi-factor authentication (MFA) far outweighs the risk of a cyber criminal getting access to an employee’s account because their password was cracked.
Multi-factor tools, such as Cisco's Duo or WatchGuard's AuthPoint, verify that someone trying to log into one of your systems is indeed who they say they are.
More information on multi-factor authentication (MFA):
- Multi-Factor Authentication: What Is It & Can Small Businesses Use It?
- Multi-Factor Authentication (MFA) Options for Businesses: What They Do, How They Work, and How Much They Cost
- Top 5 Places Businesses Should Use Multi-Factor Authentication
2. Keep Software Updated
Every software has potential cracks in it that create potential entry points for hackers. That's why keeping software updated to the latest version and replacing legacy software that’s out-of-support is so important.
Hackers are looking diligently for these holes all the time. Software developers are too. That’s why they come out with updates that patch these holes.
Updated software isn't just for PCs and laptops, but also firmware, routers, software applications, operating systems, and any other piece of equipment that’s connected to your network.
This includes the machines your employees are using when they're working from home.
3. Employing "Edge" Security and Endpoint Detection and Response (EDR)
Firewalls are another critical line of defense that organizations should use. A firewall is a type of network security system that provides a barrier between the outer "edge" of their own internal trusted network and an external non-trusted network, (e.g., the internet).
Firewalls work by monitoring and controlling all incoming and outgoing traffic between internal and external networks by adhering to a predetermined set of security rules. In layman's terms, the firewall is your network's bouncer, deciding who gets to come and go.
Modern firewalls have taken their capabilities a level up by including built-in Endpoint Detection and Response (EDR) tools. EDR uses artificial intelligence to “learn” what normal traffic on your network looks like. Then when something happens that is out of the ordinary, it can flag that activity, examine it for threats, and stop it from infecting your whole network.
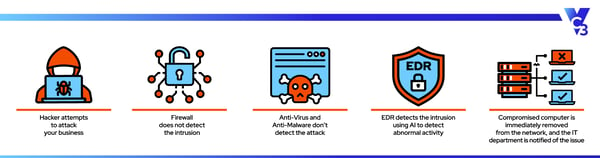
We do everything we can to prevent cyber attacks, but we're fighting an uphill battle as hackers are coming up with new ways to get in by the minute. That's why quick detection has become so important.
4. Use a DNS Filter
DNS filters have been around for a long time and they don’t get the credit that they’re due.
Compromised websites continue to be a source of malware. Using a good DNS filter, such as Cisco's Umbrella software, can prevent a security breach from happening if (when) someone accidentally clicks on a link in a phishing email.
DNS stands for Domain Name System and it’s fundamental to how the internet works. Every time your browser wants to go to a web address, it triggers a DNS query. That query matches up the web address with one or more IP (internet protocol) addresses.
A DNS filter will determine if the website in question is legitimate, or if it's on a list of known phishing and/or malicious websites. If the website is on the DNS filter’s blocked list, the user won’t be allowed to visit the site.
5. Security Training for End Users
Think that most internet security issues happen due to some type of complex technological gap?
Nope! 95% of cyber security breaches are a result of human error.
Since many employees are now working outside a traditional office setting, it's more important than ever for companies to provide their staff with sufficient training to spot potential scams, as well as define standards relating to the use of corporate equipment and software applications.
Ideally, employees should only use company-owned technology equipment for work-related purposes, and they shouldn't share this equipment with family members when working from home. They should also be vigilant about paper trails – notes, files, and any confidential information should be kept under lock and key when not in use by the employee.
Train employees on how to spot suspicious websites and emails. As with anything, telling someone once doesn’t equal “training.” Ongoing, interactive security awareness training programs like KnowBe4 give employees the regular practice they need to quickly recognize scams.
And let’s not forget about other modes of communication. Phishing and social engineering scams can take the form of an unexpected text or chat message, or even a phone call from someone pretending to be a client, a vendor, or a new employee working within the company.
Security Layers Work Together to Keep Your Network Locked Down
Assume that cyber criminals are trying to get to your people, data, and network all the time.
By implementing a layered security prevention and detection plan - comprised of training end-users to spot suspicious scams, updating technology, using multi-factor authentication, a DNS filter, and a firewall with EDR – you’re making sure that each individual tactic has a backup to counter any gaps in the other defenses.
Need Confidence in Your Security Strategy?
If you're still feeling unsure about your cybersecurity situation, we can help!
Contact us today for more on how to help your small business ward off online security threats.
Be sure to ask about our comprehensive Cyber Risk and Security Assessment. Find out FOR SURE if your IT team has all of the security layers in place that you need to stop cyber threats in their tracks.


